One of the first things a budding online entrepreneur will realize is that the content management system WordPress is the most massively used website building tool on the planet. The second thing this newbie entrepreneur will likely stumble across is more than a few disgruntled users claiming its security features are crap. Don’t let these naysayers scare you away.
A WordPress installation used in conjunction with a quality web host that specializes in securing the software can be the easiest, most effective website solution. The thing to keep in mind is that you can minimize the odds of most WordPress issues by following recommended best practices. The following are the five most common WordPress security problems.
#1. A Brute Force Attack
A brute force is a simple hacker scheme in which malicious software is deployed to enter thousands (maybe even millions) of user name/password combinations at the WordPress login screen in hopes of guessing the correct information. Since the attack is conducted with software, it never gets tired or discouraged. Brute force attacks are extremely effective but only because too many website owners don’t take a few dead simple precautions to foil them.
As a default, WordPress doesn’t limit the number of login attempts. By setting this to three or five or whatever, you cause any brute force attack to be automatically disengaged when it reaches that point. This is an EASY fix. Another way you leave yourself open to brute force hacks is by having too simple a password. Use at least an eight-digit string of upper and lowercase letters, numbers, and symbols, and don’t use the same password you use anywhere else online. Presto! Brute force issue minimized.
#2. File Inclusion Exploits
This is the second most popular way for hackers to exploit WordPress. It occurs via misuse of the PHP code, which is the file that contains the instructions that run not only plugins and themes, but the entire website. If a hacker can get into this “brain” area, he or she can cause a lot of mischief. The actual hack occurs when they find vulnerable code in the wp-config.php file. The most common way this happens is when you don’t stay on top of security updates.
If you’ve taken a look at your website dashboard much, you’ve probably seen all kinds of messages to update either WordPress itself or various plugins and themes. This is a good idea. These vulnerabilities are how file inclusion exploits occur. Check regularly for updates and apply them.
#3. SQL Injections
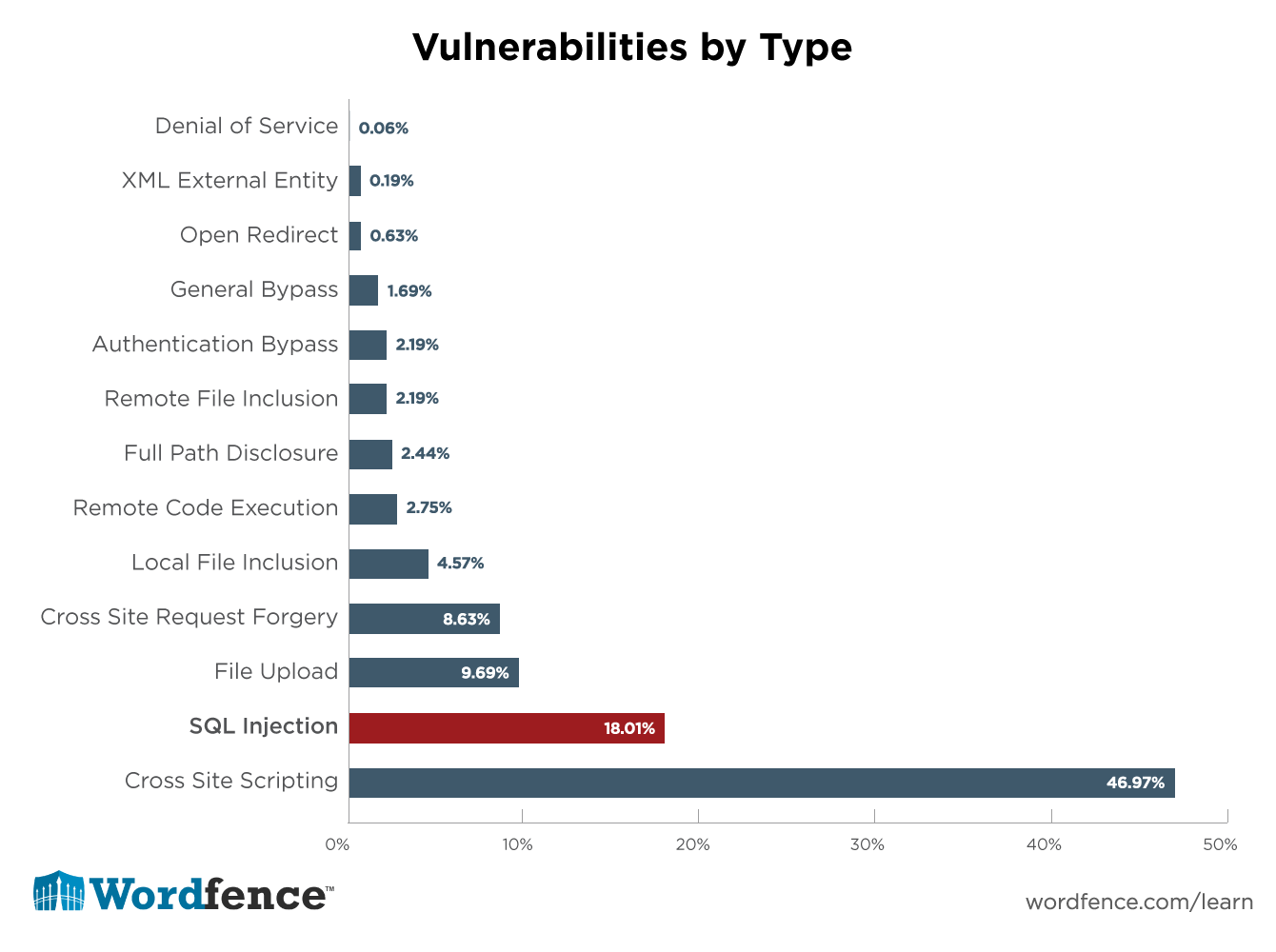
Since WordPress requires a MySQL database to operate, hackers long ago figured out that this was a perfectly serviceable backdoor into the website. Once the database is compromised, there is very little in the way of black hat operations that a skilled miscreant can’t do. How does it work?
There are a couple of common ways to penetrate a WordPress database. The first involves getting in through vulnerable code (again) in order to create a new administrator level account. Having done that, all they have to do is login and perpetrate any form of foul deed they can imagine. The second method occurs when bad code like malware or ads are injected through security breaches into the database, where they suddenly show up in the middle of your posts or pages. Though you can manually delete the junk, unless you fix the bad database code, it’ll likely just reappear. Solution? Update!
#4. Cross-Site Scripting
This nifty little technique comprises about 84 percent of all internet-related security problems. When it comes to WordPress, Cross-Site Scripting (XSS) is most commonly found in plugins. Typically, the hacker uses a plugin code vulnerability to steal information submitted in a web form. The hacker is then able to access the user’s browser and go to town from there.
Protect yourself from dangerous plugins by installing updates as soon as they are released and stay away from those that you aren’t completely sure come from a reputable source. Torrents and download sites are a bad idea when it comes to plugins. Some hackers create an irresistible plugin that claims it will perform some website task that you have been after for years. The problem is there is also a secret code backdoor through which the creator can enter your website.
#5. Your Host Might be the Problem
The truth is that some web hosts aren’t as proactive about protecting the server where your website files reside as they should be. Through laziness, overwork, or oversight, they don’t deploy the proper security measures or may forget to update software. There are a few ways to avoid these issues. The first is to do your research when evaluating a prospective web host. It’s hard to hide poor quality on the internet these days, especially in forums. The other thing is you might consider upgrading from a shared hosting account to a VPN (Virtual Private Network). Shared hosting can leave your website open to contamination from another website on the server that has been infected. A VPN allows you to keep your website files separate from other customers.
The Bottom Line
As you can hopefully surmise from this article, perceived security flaws shouldn’t keep you from considering WordPress for your website solution. While the vulnerabilities mentioned are very real, so are the ways to prevent them. Since WordPress powers one-quarter of ALL websites on the internet, it obviously is doing something right.